What Is A Cryptographic Hash Function?
A cryptographic hash function takes any sized inputs and outputs a fixed length, called the hash value, using mathematics to do so.
Compared to traditional hash functions, cryptographic hash functions have a wide array of security properties to better secure and encrypt the data being hashed.
How Does Cryptographic Hashing Work?
Hash functions are one-way, this means you can hash any input and receive the output, but cannot use the output to retrieve the input.
Cryptographic hashing functions work by running the input through a secure algorithm and dividing the input into fixed block sizes (depending on the algorithm used). Then these blocks are lumped together with the next block and so on until the whole message is hashed, where you get your output.
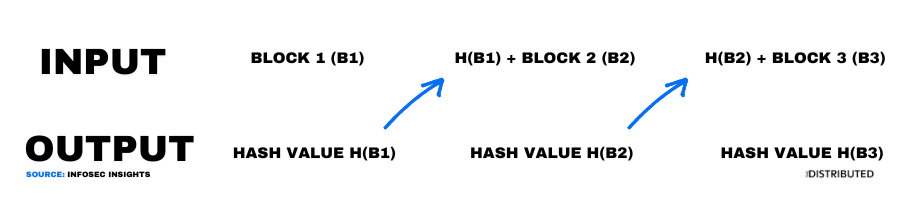
Cryptographic hash functions are deterministic, the same message will always equate to the same hash. This means that every possible combination of words and numbers can be compressed into a single fixed-length hash.
The most common hash function is SHA-256 (Secure Hashing Algorithm) below is an example of how two messages change entirely, based on one small detail.
| Input | SHA-256 Output |
|---|---|
| Hello! | 334d016f755cd6dc58c53a86e183882f8ec14f52fb05345887c8a5edd42c87b7 |
| hello! | ce06092fb948d9ffac7d1a376e404b26b7575bcc11ee05a4615fef4fec3a308b |
Cryptographic Hashing Applications
Digital Signature verification and generation use a cryptographic hash over the message. This ensures the message came from where it was meant to come from and wasn’t intercepted along the way.
Cryptographic Proofs such as proof-of-work use partial hashes to prove that work (transaction verification) has been completed in return for a reward. Validators need to perform immense amounts of work to find the valid message to confirm a block into the chain, but recipients can verify the validity of this message through a single hash function.
Password Verification is an important use of hashing. Storing passwords in cleartext along with the user can prove very dangerous in cases of network breaches. Passwords are generally stored within the network, although hashed.
Verifying Messages And Files for their integrity by comparing the hashed message before and after being sent to see if there were any changes in the hash output.